Threat Watch
Threat Watch provides an instant, sophisticated evaluation of your cybersecurity posture.
Visit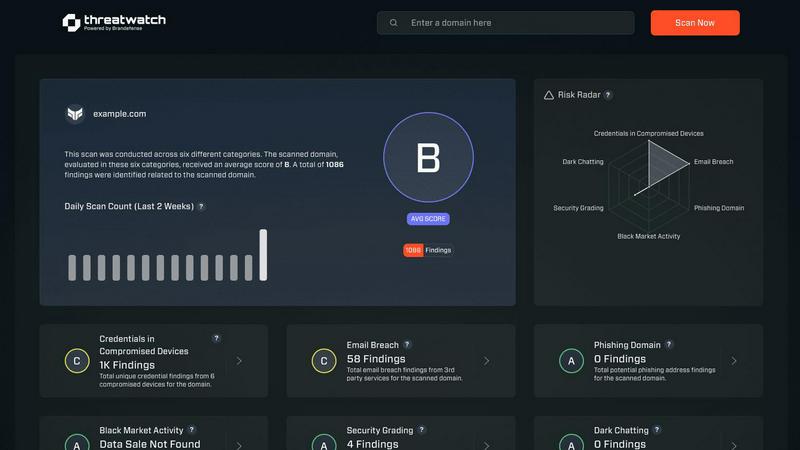
About Threat Watch
In an era defined by digital velocity and sophisticated adversaries, understanding your organization's true security posture is paramount. Threat Watch emerges as the definitive cybersecurity intelligence platform, engineered to transform fragmented data into a coherent, actionable narrative of your cyber health. It transcends traditional point-in-time assessments by providing a continuous, unified view of your assets, vulnerabilities, and exposures across the clear, deep, and dark web. Designed for security leaders, IT managers, and compliance officers, Threat Watch delivers the clarity needed to move from reactive defense to proactive resilience. Its core value lies in synthesizing vast streams of threat intelligence into a clear, prioritized dashboard, enabling organizations to identify critical risks, automate complex assessments, and implement mitigations with unprecedented speed and confidence, thereby fortifying their digital estate against evolving threats.
Features of Threat Watch
Comprehensive Cyber Health Dashboard
Threat Watch provides a centralized, intuitive dashboard that delivers a holistic and immediate visual representation of your organization's security posture. It aggregates and analyzes data across multiple critical categories, presenting a single source of truth that details asset vulnerabilities, credential exposures, and dark web mentions, allowing for at-a-glance understanding and swift executive decision-making.
Real-Time Exposure Detection
This feature continuously monitors a vast array of data sources, including breach databases, phishing feeds, and dark web forums, to identify your organization's compromised credentials, breached accounts, and phishing addresses in real time. By providing instantaneous alerts, it ensures that you are informed of exposures the moment they are discovered, drastically reducing the window of opportunity for attackers.
Automated Asset & Vulnerability Assessment
Threat Watch automates the discovery and evaluation of your digital assets and their associated vulnerabilities. It systematically scans and analyzes your infrastructure, eliminating manual effort and providing automated, consistent assessments that identify misconfigurations, unpatched software, and other security gaps that could be exploited.
Prioritized Risk Intelligence
Moving beyond simple alerting, Threat Watch employs intelligent analytics to contextualize and prioritize discovered risks. It correlates internal vulnerability data with external threat intelligence to calculate a realistic risk score, guiding your security team to focus their efforts on the most critical issues that pose the greatest immediate threat to your business.
Use Cases of Threat Watch
Proactive Breach Response and Credential Monitoring
Organizations utilize Threat Watch to proactively discover if employee credentials or corporate accounts have been compromised in third-party breaches. This enables immediate response actions such as password resets and multi-factor authentication enforcement before the stolen data can be weaponized in credential-stuffing or phishing attacks against their infrastructure.
Continuous Security Posture Management
For IT and security teams, Threat Watch serves as a continuous monitoring tool for overall cyber health. It provides an ongoing, automated assessment against key security categories, replacing costly, periodic manual audits with a living model of risk that supports compliance reporting and demonstrates due diligence to stakeholders and auditors.
Third-Party and Supply Chain Risk Assessment
Companies extend the visibility of Threat Watch to evaluate the security posture of key vendors and partners. By monitoring for exposed credentials or dark web discussions related to their supply chain, they can identify third-party risks that could serve as an entry point into their own networks, enabling more informed vendor management.
Executive and Board-Level Reporting
Security leaders leverage the clear, consolidated dashboard of Threat Watch to generate sophisticated reports for executive leadership and the board. The platform translates complex technical findings into accessible insights about business risk, facilitating informed strategic discussions and securing necessary budget for security initiatives.
Frequently Asked Questions
What does Threat Watch actually scan and monitor?
Threat Watch conducts a comprehensive scan that analyzes your organization's publicly accessible digital assets for vulnerabilities and misconfigurations. Simultaneously, it perpetually monitors a wide array of data sources, including global breach databases, phishing site feeds, hacker forums, and dark web marketplaces, for any exposure of your corporate credentials, domains, or sensitive information.
How is Threat Watch different from a traditional vulnerability scanner?
While traditional scanners focus primarily on identifying technical vulnerabilities within your defined network perimeter, Threat Watch provides a unified intelligence layer. It combines internal asset scanning with external threat intelligence (breaches, dark web data), offering context that prioritizes which vulnerabilities are most likely to be exploited based on actual adversary activity and exposure.
What kind of assets can Threat Watch discover and assess?
Threat Watch is designed to discover and assess a broad range of external-facing digital assets. This includes web applications, servers, network infrastructure, cloud instances, and associated domains. It identifies these assets and evaluates them for known vulnerabilities, open ports, misconfigurations, and exposure of sensitive data.
Is the initial scan truly free, and what does it include?
Yes, Threat Watch offers a free initial scan designed to provide immediate value. This scan typically includes a high-level assessment of your attack surface, identification of critical assets, and a preliminary check for compromised credentials and known vulnerabilities, delivering a snapshot of your cyber health without any upfront commitment.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt simplifies contract management with secure templates, swift signing, and automated reminders for seamless colla...
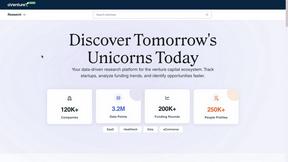
aVenture
aVenture delivers institutional-grade venture intelligence to research private companies and map the competitive land...